New OpenID User and Identity Provider Configuration
Scenario: You want to create and configure a new Identity Provider to associate with an OpenID (OpenID Connect or OIDC) user.
In this workflow, you must request credentials from the Identity provider of choice, and then use those credentials in Desigo CC to configure a new Identity Provider and then associate OpenID users with the configuration.
In Desigo CC the OpenID user account is used in conjunction with configuring Identity Providers to securely access the Flex client.

NOTE:
OpenID accounts are only applicable for accessing the Flex client.
Reference: For background information see the reference section.
Workflow diagram:
Prerequisites:
- System Manager is Engineering mode.
- System Browser is in Management view.
Steps:
If you already have an identity provider account, you can skip this step. However, make sure you have the identity provider’s credential’s handy (see Step 2 in this procedure.)
- You must have the Flex client project URL available to register your project.
- Register the project with the identity provider and publish the redirect URL from the Desigo CC Web Service Interface.
- From the Identity provider email, note the following information that you will need when you configure the Desigo CC identity provider information in the next step of this workflow:
- Domain
- ID Server Domain
- Client id
- Client secret
- Connection name
- For more information, see the identity provider configuration example: Example: Auth0 Identity Provider Configuration.
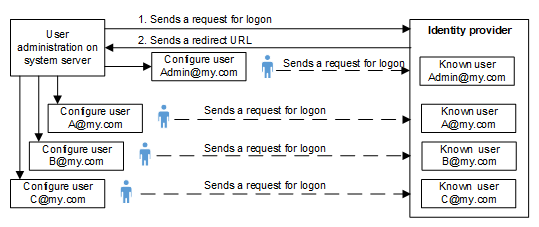
You want to configure an Identity Provider to associate with an OpenID user(s).
- System Manager is in Engineering mode.
- System Browser is in Management View.
- Select Project > System Settings > Users.
- Select the Identity Providers tab.
- From the toolbar, click Add New
 .
.
- The Name dialog box displays.
- Enter the name for the Identity Provider configuration, and then click OK.
NOTE: The OK button is grayed out when the name contains an invalid character or the name already exists in the Identity Provider Configuration list. Additionally, if the name already exists, the entered text displays in red. The following are valid characters for the configuration name: alphanumeric, “_” and “-”.
- The blank Identity Provider Configuration and Endpoints sections display.
- In the Identity Provider Configuration section Type or copy the information from the Identity Provider email from the previous step in this workflow and paste it into the following fields accordingly:
- Domain – Type or paste the value in the following format: abc.def.xyz.
- ID Server Domain – Type or paste the value in the following format: abc.def.xyz.
This value is used during the logout workflow.
NOTE: In some cases, the Domain and ID Server domain links may be the same. Some Identity Providers have a different ID Server Domain. In this case, provide the specific ID Server Domain here.
- Client id
- Client secret
- (Optional) In the Connection name field, paste the Connection Name obtained from the Identity Provider.
NOTE: Whenever users log into Desigo CC using OpenID user account, this connection is used as a default connection and users will be navigated directly to the Authentication page of the connection. For example, google-oauth2, LinkedIn, and so on. If no value is provided, users need to perform one additional step and select the appropriate connection to authenticate from Auth0 default logon page.
- The Default endpoints checkbox is checked by default and the endpoint values are automatically populated. To manually enter the endpoint values, uncheck the checkbox and enter the values for each endpoint.
- Click Save
 .
.

NOTE:
The URL links refer to API addresses. When clicked, a browser window with an error message will display. It is, however, possible to check the connection to the server.
NOTE: OpenID accounts are only for logging into the Flex client.
- System Manager is in Engineering mode.
- In System Browser, select Management View.
- Select Project > System Settings > Users.
- Select the Users tab.
- Click New
 .
.
- The New User dialog box displays.
- From the User type drop-down-list, select OpenID account.
- From the Identity Provider drop-down list, select the name of the Identity Provider configuration you created in the previous step.
- In the User name field, enter a valid email account for the associated user.
NOTE: This email account must register using his or her e-mail address and a password with the Identity Provider with an account
- Click OK.
- Select the Enabled check box for the user.
- Click Save
 .
.
- The user is created, but not configured.
- In the Users tab, select the Configured Groups expander and select the appropriate user group from the User Group list.
- Drag-and-drop the user group to the User Configuration list.
- The user group is moved from Configured Groups list to the Group Membership list.
- Repeat steps 1 and 2 for additional user groups that you want to assign to the user.
- The user groups are assigned to the user.

NOTE:
Assigning user groups to users is the same as assigning users to user groups, so the assignment can be performed in either section.
- In the User Settings expander, do the following:
a. Under Language, select the appropriate language.
b. Under Client profile, select the corresponding user profile to layout Desigo CC.
NOTE: The correct schema for your region is assigned to the project. The schema contains the mapping of categories, events and colors for the representation of the Alarm Summary bar.
- In the User Information expander, do the following:
a. In the Full name field, enter an expanded user description. This text displays as the user name on the Summary bar.
b. In the Comment field, enter an expanded description.
- Click Save
 .
.
- The user is enabled and can log on to the Desigo CC Flex client.
- A history log entry is created for each enabled user.

NOTE:
You can disable a user at any time if you have the appropriate user rights. Clear the Enabled check box.
- Enter the project Flex Client URL in the browser.
- From the Flex Client login pane, in the Username field, enter the OpenID user account email name. Click Next.
- Depending on the connection used, Desigo CC navigates you to the authentication page of the Identity Provider.
NOTE: If you have been authenticated by the Identity Provider on that host before, this authentication step is skipped. In this case, the Desigo CC server and the Identity Provider exchange tokens and provide access. This scenario is also known as Single Sign-On (SSO).
- Log in to the Identity Provider.
- You are logged into Desigo CC depending on the authentication results.
- When you log out of the Flex client, you are logged out from Desigo CC and the Identity Provider. If the client workstation the Flex client is connected to is marked as “Privately used” then logging off from the Flex client only performs a logoff from the Flex client and not the Identity Provider.
NOTE: With Desigo CC version 6.0, when you log in to the Flex Client application using an Identity Provider, you must log out of the Flex client and the Identity Provider independently. However, if you are logged in to the Flex client with MyId (Siemens ID) via Auth0, then a single logoff from the Flex client applies to both the Flex client and the Identity Provider.
NOTE: We recommend that you clear both the history and cache in the browser and close the browser instance after you log off from the Flex Client.
