Security Configurations - Deployment Scenarios
Before installation, you choose a deployment scenario as per your requirement. You also need to consider accordingly the software requirements such as the Microsoft SQL database and the web server (IIS) that you will connect to, the ports in the firewalls that must be open and so on.
Additionally you also need to review the hardware requirements for setting up the system in various deployment scenarios. For this you need to refer the System Description (A6V10415500 ).
Following are the deployment scenarios with their security configurations:
The following describes a stand-alone configuration, where the Desigo CC server and the Desigo CC Installed client are located on a single computer.
In this scenario, Windows App clients are not involved.
What is a Stand-Alone System?
A single dedicated workstation that runs both the Desigo CC server and the Desigo CC client application, typically communicating with a field system in a networked environment. It includes the following features:
- Own administration
- Microsoft SQL installed locally
- IPv4
- No IT firewalls in-between Desigo CC components (since there are no remote clients, firewalls do not need to be opened for communication)
Security
- Simple setup (certificate configuration not required).
- Effort for security configuration is low.
- A stand-alone system is secure in regards to attacks from the outside. However, installation guidelines for closing outside communication by firewall settings, virus scanner, and backup must be followed to secure the system.
Deployment Diagram

Desigo CC Server with Installed Client and Microsoft SQL Server
The following describes a typical deployment scenario for setting up a Desigo CC system with a local web server (IIS) on a single computer.
What is a Local Web Server?
The Windows App client option requires installing an optional web server component (IIS). When the web server (IIS) is installed on the same computer as the Desigo CC server, it is called the local web server (IIS).
What is a Stand-Alone System with a Local Web Server?
A local web server is a single dedicated workstation with the following features:
- Desigo CC Server
- Web server (IIS)
- Own administration
- Microsoft SQL installed
- Accessed by means of Windows App client
- Intranet, own network segment
- IPv4
- No IT firewalls (to other network segments or to the Internet)
Security
- Simple setup
- Effort for security configuration is medium
- A stand-alone system with a local web server must be protected against attacks from other machines in the network. Follow the configuration guidelines to limit outside communication by firewall settings, virus scanner, and so forth to secure the system.
Certificate Usage on a Stand-alone System with a Local Web Server
- No certificate is required for the communication between the Desigo CC server and the installed client or FEP since there is no FEP and no remote installed client in this deployment.
- The communication between the Desigo CC server and the local web server (IIS) can be left unsecured (without certificates), since they are both installed on the same machine.
- The communication between the web server and Windows App clients is always secured. Hence, the Web site and the web application creation certificates are mandatory. Desigo CC supports using either the same or different certificates for the web site and the web application. This section describes how to configure the web server using the same certificate for both the web site and the web application.
- The certificate and its private key must be imported into the Windows certificate store (in the Local machine\Personal store; its root certificate must be imported in the Local machine\Trusted Root Certification Authorities (TRCA) store). The private key must be marked as exportable.
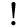
Validity of Self-Signed Certificates
Self-signed certificates allow local deployments without the overhead of obtaining commercial certificates. When using self-signed certificates, the owner of the Desigo CC system is responsible for maintaining their validity status, and for manually adding them to and removing them from the list of trusted certificates.
Self-signed certificates must only be used in accordance with local IT regulations (several CIO organizations do not allow them, and network scans will identify them). Importing the commercial certificates follows the same procedures.
You must ensure the compliant installation of the trusted material on the involved machines, for example, on all Installed Clients. In some organizations, this must be done by the IT organization.
Deployment Diagram

A Desigo CC installation has only one server, but it can have multiple clients, running on different computers. You can work with Desigo CC in configuration where a Desigo CC server communicates with multiple Desigo CC clients installed on separate computers. This allows multiple operators to manage and supervise the same site.
The communication between the client and the server must be set up using the SMC. First, you must set up the server and then the client station. The communication should be secured using certificates (this might be simplified on dedicated and protected networks, such as within a control room).
By default, the template project is created for a stand-alone configuration (with the indication that no communication is possible). To set up a secured/unsecured client/server system, you must edit the project.
Server Station
A dedicated workstation with the following features:
- Desigo CC server
- Own administration
- Microsoft SQL installed/remote customer MS SQL
- Own network segment
- IPv4/IPv6
- IT firewalls must allow communication between server and client
Client Station
A dedicated workstation with the following features:
- Desigo CC client/FEP
- Own administration
- IPv4/IPv6
- Internal firewalls
Security
- Secure client/server deployments require medium configuration setup.
Certificate Usage
This scenario explains setting up a secured client/server communication using certificates from the Windows store.
For a client/server deployment, the following restrictions apply with respect to certificates:
- The root certificate identifies the source of certificates used for communication. Therefore, they must be the same for all host certificates and must be available to the server and all clients.
- The root and communication (host) certificates must be different and have different subject names.
- The communication certificates should be specific. Therefore, it is recommended to use different host certificates for client and server.
- The communication certificates are used by the Desigo CC client/FEP. Therefore, the logged-on user of the client/FEP operating system requires access to the private key of the host certificate stored in the Windows Certificate store.
- If a remote FEP is connected to the Server, it must have the same Windows key file is available in the Windows Key Store.

The owner of the Desigo CC system is responsible for distributing authorized certificates and keys. This is often done by the IT infrastructure, particularly, if commercial certificates are used instead of the self-signed ones.
Deployment Diagram
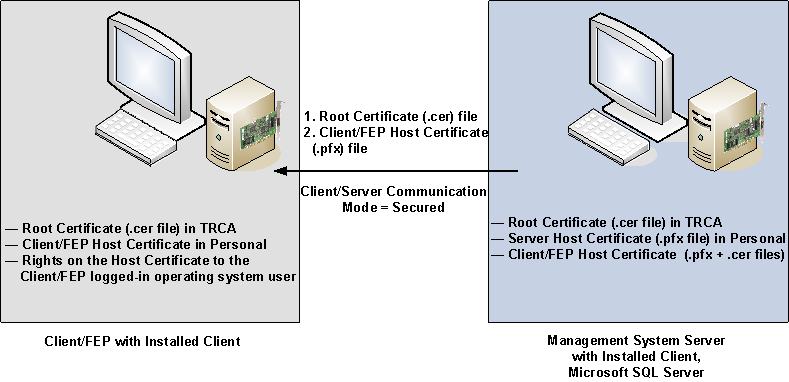
This section describes a typical deployment scenario for setting up a Desigo CC system with the web server (IIS) installed on a separate computer.
Server Station
A single dedicated workstation with the following features:
- Desigo CC server is installed.
- Microsoft SQL is installed on the Desigo CC server.
- The server project folder is shared.
- The required certificates (SMC created or commercial) are imported in the Windows Certificate store:
- The root certificate is imported in the Trusted Root Certification Authorities store.
- The host certificate and its private key are imported in the Personal store.
- The host certificate used must have a private key; no private key is needed for a root certificate.
Remote Web Server (IIS) Station
- The Windows App client requires installing an optional web server (IIS) component. When the web server (IIS) is installed on a separate computer known as the remote web server (IIS).
- A remote web server (IIS) hosts web sites and web applications. To simplify the web site configuration using SMC, it is recommended that you also install the Desigo CC client (or FEP) component on this machine.
- The web application user on this remote web server has access rights on the shared project folder on the server.
- The required certificates (SMC created or commercial) are imported in the Windows Certificate store:
- The root certificate of the host certificate provided for CCom port security is imported in the Trusted Root Certification Authorities store.
- The communication between the web server and the Windows App clients is always secured. Hence, the web site and the web application creation certificates are mandatory. Desigo CC supports using either the same or different certificates for the web site and the web application. This chapter describes how to configure the web server to use the same certificate for both the web site and the web application.
- When a commercial certificate is used for creating a web site and web application, then ensure the following:
- The commercial self-signed certificate must be imported in the Trusted Root Certification Authorities and Personal stores of the Local machine store.
- The commercial host certificate, along with its private key, must be imported in the Personal store and its root certificate must be imported in the Trusted Root Certification Authorities store of the Local machine store.
- You can also configure a remote web server (IIS) as an Installed Client/FEP. This will allow you to perform the Client/Server deployment scenario. For more information, see client/server deployment scenario.
Security
- Secure server/remote web server (IIS) deployments require medium security configuration setup.
Deployment Diagram
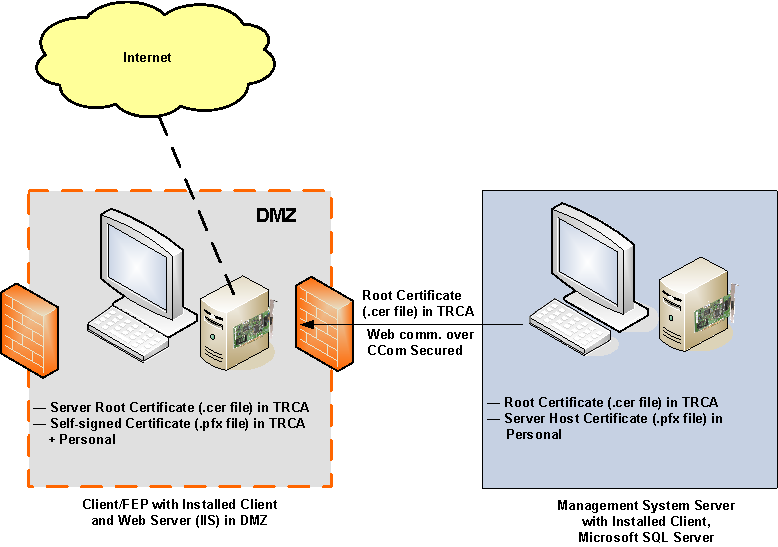
A DMZ (demilitarized zone) refers to an area of a network, usually between two firewalls, where users from the Internet are permitted limited access over a defined set of network ports and to pre-defined servers or hosts. A DMZ is used as a boundary between the Internet and your company's internal network. The network DMZ is the only place on a corporate network where Internet users and internal users are allowed at the same time.
In a DMZ setup, the web server (IIS) and the Desigo CC server are hosted on separate machines that are on different networks, separated by firewalls.
In such a scenario, commercial SSL certificates are typically used for the web site on IIS. For verifying the signature of the Windows App client, the same certificate or a separate commercial or self-signed certificate, may be used. However, you can use the same certificate if the private key used to secure the web site is exportable.
The following section describes a typical deployment scenario for setting up a Desigo CC system with a remote web server (IIS) in a DMZ scenario.
Server Station
A single dedicated workstation with the following features:
- Desigo CC server is installed.
- Microsoft SQL is installed on the Desigo CC server.
- The server project folder is shared.
- The required certificates are imported in the Windows Certificate store:
- The root certificate is imported in the Trusted Root Certification Authorities store.
- The host certificate is imported in the Personal store.
- The host certificate used must have a private key; no private key is needed for a root certificate.
Remote Web Server (IIS) Station in a DMZ
- A dedicated workstation serving as web server for hosting the web site/application. To simplify the web site configuration, it is recommended that you install the Desigo CC client or FEP software on this machine.
- The web application user on the remote web server has access rights on the shared project folder on the server.
- The required certificates are imported in the Windows Certificate store:
- The root certificate of the host certificate provided for CCom port security is imported in the Trusted Root Certification Authorities store.
- The communication between the web server and the Windows App clients is always secured. Therefore, creating the web site and the web application certificates are mandatory. Desigo CC supports using either the same or different certificates for the web site and the web application. This section describes how to configure the web server to use the same certificate for both the web site and the web application.
- The certificate and its private key must be imported into the Windows certificate store (in the Local Machine\Personal store; its root certificate must be imported in the Local Machine\Trusted Root Certification Authorities (TRCA) store). The private key must be marked to be exportable.
- If different commercial certificates are used for creating the web site and web application, then both must be present in the Trusted Root Certification Authorities store and the Personal store of the Windows Certificate store.
Security
- Secure server/remote web server (IIS) deployments require high security configuration setup.
Deployment Diagram